If you happen to have an ESXi which needs to be in hosting, or some remote network where you cannot have a firewall protecting you ESXi installation this guide might be of help to you.
In such situation you have two options to go with:
- Give the ESXi host the public IP given by your ISP and rely on it firewall setting (which is not feasible if you only have one IP address)
- Install a firewall as a VM on the ESXi host and use that
The first solution is not a winner if you’ve got only one public IP assigned by your ISP as you need to purchase more for your VMs.
The second option can be handy, but it has a significant drawback, namely that if your firewall VM would not start, then you won’t be able to access your ESXi. To be honest in many cases you cannot do anything anyway if the host is not able to start up the VMs. This is usually due to a hardware failure which needs manual intervention either via an IP KVM or physically being on site.
So let’s try to sum up the goals and the planned solution:
- We want to have our ESXi behind a firewall
- We want to have VPN access to it’s management address (either site-to-site or RA or both)
The network diagram will look like this:
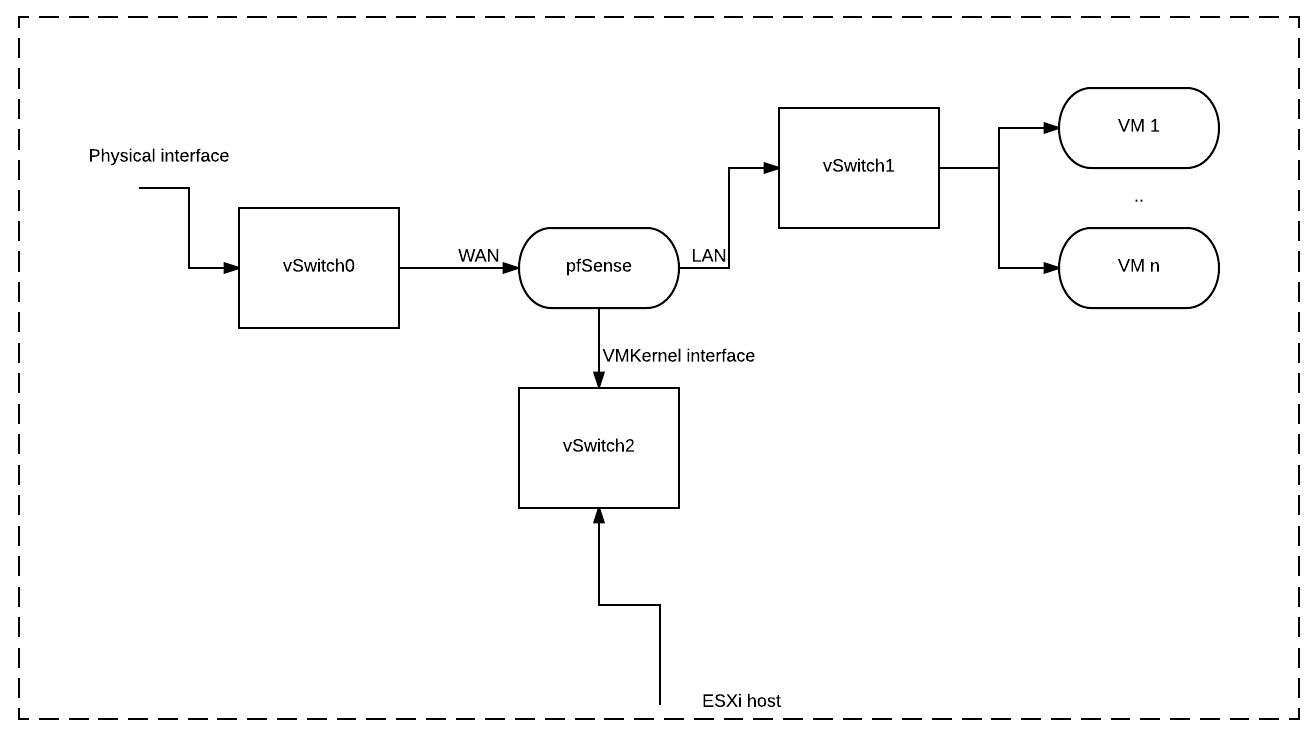
As the above diagram shows you need to create 3 standard vSwitches for this to work. You will need to attach 3 interfaces to the pfSense VM and name the third one as “VMKernel” for the ease of understanding. You can stick with the default “OPT1” but it’s easier to understand the layout later if you go with “VMKernel”.
You attach only the WAN interface to your outside switch (vSwitch0) which then in turn can have your single associated IP address from your provider.
The next step is to assign your LAN interface to the inside switch (vSwitch1). This will be the interface looking towards your further VMs which likely to need to access the internet. Now that you have a WAN and a LAN interface you can easily set up a standard outgoing NAT from LAN -> WAN. Additionally you can set up some port forwards from WAN -> LAN too.
The last step is to attach your VMKernel interface to your third switch (vSwitch2) which will have the VMKernel interface of your ESXi host attached. The default GW and other setting will be matching your pfSense VMKernel address space and surely can be private range.
From here on, it’s easy to add IPSec, OpenVPN or any other kind of access from WAN -> VMKERNEL so you can access your ESXi. Same way you can set up access to your servers to if you need to.
If you have multiple IP addresses from your provider, you can add them to your pfSense’s WAN interface. The method will depend on how the IP addresses are given to you. The good thing is that now you can act as a router and ask your ISP to route all your addresses to your WAN IP or simply just add them as IP aliases.
The setup works perfectly well in an IPv6 context too. Depending how you get the range, either an additional /64 or less can be routed to your outside IPv6 address or you can use an IPv6 tunnel broker like HE.net. If you do, just set it up on your pfSense as you normally would and they will provide a default /64 and you can get a /48 with one click. If you want to access your ESXi through IPv6 in this case you simply add the /64s to your inside interfaces (VMKernel, LAN) and the appropriate FW rules, and you can access all your resources.
As a last step make sure that your pfSense VM is set to automatic startup with the highest priority in ESXi so upon an eventual reboot you get the VM up and running first.
If you have a vDS setup, however the concept is adaptable you less likely to do something like this as you will have more than one ESXi host, etc.
I hope this made sense and was helpful. If you have any questions, let me know.
PS: Worth mentioning that the setup works with any other firewall product really (even just a simple Linux/BSD box with your custom firewall). The concept is the same. To be honest it works with different Hypervisors too.
